Papers I read recently, part 1
August 1, 2025
I read these papers over the spans of a few Sundays at playspace, which has now ran its very last session. I'm grateful to the hosts who have made space for me to show up Sundays after Sundays so I can eat some snacks, meet cool people and read the papers I want to share here.
1. On Being a ~~Computer Scientist~~ Human Being in the Time of Collapse
2. Apple's CSAM Detection Technical Summary
3. The Right to Oblivion: Privacy and the Good Life
On Being a Computer Scientist Human Being in the Time of Collapse
I came across this paper while researching authenticated encryption schemes. Rogaway, a cryptography professor, delivers sharp criticism of technologists' "central and overwhelmingly negative role" in contemporary issues: surveillance capitalism, democratic erosion, and increasingly sophisticated remote warfare.
He argues that the abstraction model that is so effective in computer science for defining boundaries and scope fails catastrophically when applied to ethical problems. We allow ourselves to avert our gazes. This unbridled, relentless optimism and solutionism creates empowerment but its byproduct is an invincible illusion that our expertise in technology somehow morally licenses us to remain apolitical—to not care about the external, real world.
"Whether or not you care about any of this stuff [social, political problems] is ultimately irrelevant, because technological advance will inevitably see us through. In this way we depoliticize our current crises."
In this climate of increasing militarization of tech, this paper resonates. This industry isn't what it was 5 years ago. I thought a long time about this paper and strangely it reminded me of Ken Thompson's paper Reflections on Trusting Trust. At the end of the day, you have to trust something, someone, an identity, an entity. We want to live in a world where the people who make the things that we depend on and consume are good, but not just good, that they have faith in the world and that they care about us. The foundation of that trust cannot be cynical because at face value, cynicism is counterproductive. On the flip side, that trust has to be earned and this industry is quickly running out of un-earned trust. Rogaway posed a bleak but reasonable problem with the way we, as technologists, operate.
You can't make the world better by being angry at it but honesty is the right first step. Anyways, the trees are calling me, let's move on to the next paper.
Apple's CSAM Detection Technical Summary
Rogaway said that he loved cryptography because "cryptographic mechanisms are mathematical snowflakes." To me, it's the mathematical equivalent of finding out that penicillins can treat infections - you discover something that already exist and you find the perfect use case for humanity. To that end, CSAM detection is the perfect application of this beautiful math.
Now Neural Hash, the algorithm used in this paper, is not classical cryptographic hashing. It uses a convolutional neural network to evaluate the image, then some hashing for compression to produce some 96 bits. (This paper came out in 2021, this value can in fact be corrupted or bypassing detection by adding noise.)
As far as secrets system design goes, this is fascinating. Apple receives NeuralHashes of known violating images from child-safety organizations. The hashes then get transformed and blinded with a server-side secret using elliptic curve cryptography. The hash table for look up is stored on device but the result of the match is only known on the server. This is Private Set Intersection or PSI.
Even if there is a match, the content of the user images is completely opaque to Apple until an n number of matching images are detected. This is called Threshold Secret Sharing.
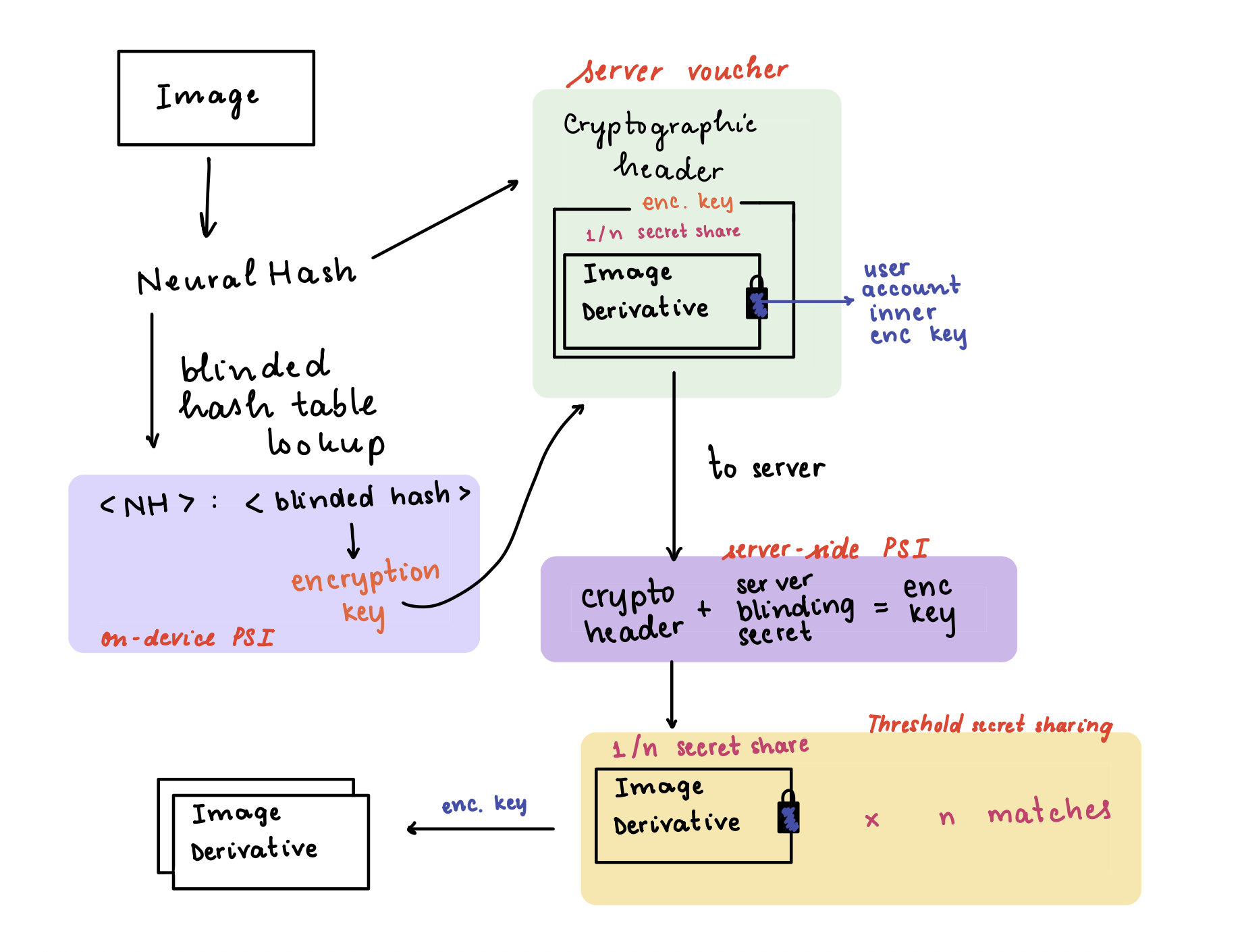
A high level overview of the PSI and Threshold Secret Sharing systems
Apple has since dropped this scanning in favour of end to end encryption. This threshold voucher system is still a great example of balancing user privacy while protecting children's safety. This is also relevant to the ongoing anti-encryption movement to introduce backdoors to encryption systems in the name of public safety. This is a short read and doesn't require that much knowledge on cryptography if you are looking for an entry paper to applied cryptographic systems.
I started researching this from my conversation with Sarah. She spent all of her internships in child safety engineering fighting the bad guys on Facebook, Microsoft and X. She's graduating soon and is looking for a new grad role in Trust Engineering. She is as kind and funny as she is talented, any team would be lucky to have her.
The Right to Oblivion: Privacy and the Good Life by Lowry Pressly (book)
If someone watched you through a vent in your hotel room, they never told anyone and you never found out. What privacy did you lose?
In this book, Pressly explored the philosophical roots of privacy by advocating for oblivion. This, he defined as the part murky, unaccounted for parts of our inner worlds that is beyond our self-knowledge. From the photographic invasion of privacy in the 19th century to romantic relationships, the book explores how privacy allows human flourishing as it allows us to escape the shallow fixity of our collected data, into the vast seams of our existence.
All this means that for human agents, living a life takes persistent effort. You have to keep it up, if you would be anyone at all.
Maybe it's because I haven't read philosophy since high school but reading this book feels like reaching out your hands to grasp something immaterial. Pressly circumvented the conversation around tech surveillance with a meditation on why privacy is a dignified refuge from the rigidity of personhood. It essentially answered the same question as if you could know your fortune, would you. It bridged the gap between privacy and personhood in a precise way that I haven't seen before but I did leave it wanting more.
Thank you for reading. I'm hoping to make this a multi-part series, here's what next on my reading list. If you're reading any of these, let me know!
- a personal computer for children of all ages
- Private Web Search with Tiptoe
- Scalable Private Search with Wally
- The Moral Character of Cryptographic Work
- Zanzibar